a6d9675d60 contrib: Ask for captcha in signet getcoins.py (W. J. van der Laan)
Pull request description:
As the faucet will always ask for a captcha now, the current script is no longer usable.
Change the `getcoins.py` script to print the captcha in dot-matrix to the terminal, using unicode Braille characters.
```
$ ./getcoins.py -a tb1q9srj96uj4uk5gva9k7h2zxuy6ttu7ltsagu0gl
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠙⠢⢄⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠑⠢⣄⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣀⠴⠊⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⢦⣄⣀⠀⠀⠀⠉⠒⠤⣀⠀⠀⢀⣀⠄⠀⠀⠀⠀⠀⢀⣀⣀⣤⣄⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⠤⠊⠁⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠹⣍⠹⣦⡀⠀⠀⠀⢀⡿⢻⣿⣿⠋⠀⠀⠀⠀⢸⠋⢩⣤⣴⣿⠃⠀⠀⠀⠀⠀⠀⠈⡟⠓⠒⠒⠖⠒⢛⣿⡖⠀⠀⠀⠀⠀⡶⠒⠛⠛⠒⠒⠶⣄⠴⠊⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⢳⡈⢻⣄⠀⣰⠏⣴⣿⠟⠀⠉⠓⠢⢄⣀⣸⡀⢸⣿⠋⠉⠀⠀⠀⠀⠀⠀⠀⠀⣧⠀⣿⣿⣿⠿⠿⠟⠃⠀⠀⠀⠀⠀⣷⠀⣾⣿⡿⣷⠊⣿⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠙⣆⠹⣾⢃⣾⣿⠋⠀⠀⠀⠀⠀⠀⢸⣟⡓⣾⣟⣯⡄⠀⠀⠀⠀⠀⠀⠀⠀⡿⠐⣛⡛⠛⠲⣄⠀⠀⠀⠀⠀⠀⢀⡸⣷⡻⢯⡤⢟⣼⣿⠃⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠘⣧⢠⣾⡿⠁⠀⠀⠀⠀⠀⠀⠀⠀⢸⡇⣿⣿⠛⠏⠓⠒⠤⠤⣀⣀⣀⠀⠛⣿⡿⠿⠿⣆⣹⣧⡠⠤⠔⠒⠉⠁⣰⠟⣥⣶⣶⣌⠹⣇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⡿⢸⣿⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⢸⡇⣿⣿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠉⣉⠉⠉⠉⢉⡏⢸⣿⡀⠀⠀⠀⠀⠀⡟⢸⣿⠏⠉⢹⡆⣻⣇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⡇⠈⣿⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⢸⠀⣿⣿⠀⠀⠀⠀⠀⠀⠀⠀⠀⣼⠛⠳⠶⠶⠛⣁⣼⣿⡇⠀⠀⠀⠀⠀⣧⠈⠻⠶⠶⠛⣀⣿⣿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠉⠿⠿⢷⠀⠀⠀⠀⠀⠀⠀⠀⠀⠛⠿⠿⠿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠘⠻⠿⣿⣿⣿⣿⡿⠿⠀⠀⠀⠀⠀⠀⠈⠻⠿⣿⣿⣿⣿⣿⠿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
Enter captcha: Yf58
Payment of 0.00100000 BTC sent with txid e0a96a2a768d1ae0d22eaa2942476927d956445276bdf508dfd2f0e2e836f300
```
The only added dependency is that `convert` from ImageMagick (or compatible fork) is installed.
Captchas are disabled by default for custom faucets, but it is possible to specify a custom captcha URL on the command line.
Also adds a way to change the amount requested with e.g. `-n 0.1`.
Edit: credit where credit is due, yope gave me the idea of using Braille characters as a widely available way to do graphics in the terminal. Another possibility is `2x2` block characters but it is a lot less compact. Yet another one is [VT340 Sixel graphics](https://en.wikipedia.org/wiki/Sixel) but it's not supported in many terminal emulators.
ACKs for top commit:
kallewoof:
Tested ACK a6d9675d60
dunxen:
Tested ACK a6d9675
lsilva01:
Tested ACK a6d9675d on Ubuntu 20.04 with the command below:
shaavan:
ACK a6d9675d60
stratospher:
Tested ACK a6d9675 on macOS 10.15.7. This PR:
theStack:
tACK a6d9675d60♟️
Tree-SHA512: 6b39cadcc42b41289977daa523c849d0b1e194ff385a7828ca0097efc0b4d7c74d1ebd3f5b274762563cf039f5198ce22a3ea8cfaa8ac3b9f9c9a954fe43d457
2d0279987e util: Make sure syscall numbers used in profile are defined (W. J. van der Laan)
8289d19ea5 util: Define SECCOMP_RET_KILL_PROCESS if not provided by the headers (W. J. van der Laan)
Pull request description:
Looks like we've broke the GUIX build in #20487. This attempts to fix it:
- Define `__NR_statx` `__NR_getrandom` `__NR_membarrier` as some kernel headers lack them, and it's important to have the same profile independent on what kernel is used for building.
- Define `SECCOMP_RET_KILL_PROCESS` as it isn't defined in the headers.
ACKs for top commit:
practicalswift:
cr ACK 2d0279987e
Tree-SHA512: c264c66f90af76bf364150e44d0a31876c2ef99f05777fcdd098a23f1e80efef43028f54bf9b3dad016110056d303320ed9741b0cb4c6266175fa9d5589b4277
021f86953e [style] Run changed files through clang formatter. (Amiti Uttarwar)
375750387e scripted-diff: Rename CAddrInfo to AddrInfo (Amiti Uttarwar)
dd8f7f2500 scripted-diff: Rename CAddrMan to AddrMan (Amiti Uttarwar)
3c263d3f63 [includes] Fix up included files (Amiti Uttarwar)
29727c2aa1 [doc] Update comments (Amiti Uttarwar)
14f9e000d0 [refactor] Update GetAddr_() function signature (Amiti Uttarwar)
40acd6fc9a [move-only] Move constants to test-only header (Amiti Uttarwar)
7cf41bbb38 [addrman] Change CAddrInfo access (Amiti Uttarwar)
e3f1ea659c [move-only] Move CAddrInfo to test-only header file (Amiti Uttarwar)
7cba9d5618 [net, addrman] Remove external dependencies on CAddrInfo objects (Amiti Uttarwar)
8af5b54f97 [addrman] Introduce CAddrMan::Impl to encapsulate addrman implementation. (Amiti Uttarwar)
f2e5f38f09 [move-only] Match ordering of CAddrMan declarations and definitions (Amiti Uttarwar)
5faa7dd6d8 [move-only] Move CAddrMan function definitions to cpp (Amiti Uttarwar)
Pull request description:
Introduce the pimpl pattern for AddrMan to separate the implementation details from the externally used object representation. This reduces compile-time dependencies and conceptually clarifies AddrMan's interface from the implementation specifics.
Since the unit & fuzz tests currently rely on accessing AddrMan internals, this PR introduces addrman_impl.h, which is exclusively imported by addrman.cpp and test files.
ACKs for top commit:
jnewbery:
ACK 021f86953e
GeneFerneau:
utACK [021f869](021f86953e)
mzumsande:
ACK 021f86953e
rajarshimaitra:
Concept + Code Review ACK 021f86953e
theuni:
ACK 021f86953e
Tree-SHA512: aa70cb77927a35c85230163c0cf6d3872382d79048b0fb79341493caa46f8e91498cb787d8b06aba4da17b2f921f2230e73f3d66385519794fff86a831b3a71d
Define the following syscall numbers for x86_64, so that the profile
will be the same no matter what kernel is built against, including
kernels that don't have `__NR_statx`:
```c++
#define __NR_statx 332
#define __NR_getrandom 318
#define __NR_membarrier 324
```
44d77d2213 sandbox: add copy_file_range to allowed filesystem syscalls (fanquake)
ee08741c9c sandbox: add newfstatat to allowed filesystem syscalls (fanquake)
Pull request description:
Similar to #23178, this is a follow up to #20487, which has broken running the unit tests for some developers. Fix this by adding `newfstatat` to the list of allowed filesystem related calls.
ACKs for top commit:
achow101:
ACK 44d77d2213
laanwj:
Code review ACK 44d77d2213
practicalswift:
cr ACK 44d77d2213
Tree-SHA512: ce9d1b441ebf25bd2cf290566e05864223c1418dab315c962e1094ad877db5dd9fcab94ab98a46da8b712a8f5f46675d62ca3349215d8df46ec5b3c4d72dbaa6
ef15c574ff build: add python3.10 alias to AC_PATH_PROGS call in configure (fanquake)
Pull request description:
Python 3.10 is [now released](https://pythoninsider.blogspot.com/2021/10/python-3100-is-available.html), and has been available as a beta/rc in distros for a little while already.
ACKs for top commit:
MarcoFalke:
cr ACK ef15c574ff
laanwj:
Code review ACK ef15c574ff
hebasto:
ACK ef15c574ff, I have reviewed the code and it looks OK, I agree it can be merged.
Tree-SHA512: 4d503d43dfbe210ac6180c63276d4ebe1aa39b0ada2a36c1292634f86603c385179b3034759441401a9ee5022f7687ccd5f3432be5c4e63f2eba7ddb76f5cbb9
9d0379cea6 consensus: use <cstdint> over <stdint.h> in amount.h (fanquake)
863e52fe63 consensus: make COIN & MAX_MONEY constexpr (fanquake)
d09071da5b [MOVEONLY] consensus: move amount.h into consensus (fanquake)
Pull request description:
A first step (of a few) towards some source code reorganization, as well as making libbitcoinconsensus slightly more self contained.
Related to #15732.
ACKs for top commit:
MarcoFalke:
concept ACK 9d0379cea6 🏝
Tree-SHA512: 97fc79262dcb8c00996852a288fee69ddf8398ae2c95700bba5b326f1f38ffcfaf8fa66e29d0cb446d9b3f4e608a96525fae0c2ad9cd531ad98ad2a4a687cd6a
4747da3a5b Add syscall sandboxing (seccomp-bpf) (practicalswift)
Pull request description:
Add experimental syscall sandboxing using seccomp-bpf (Linux secure computing mode).
Enable filtering of system calls using seccomp-bpf: allow only explicitly allowlisted (expected) syscalls to be called.
The syscall sandboxing implemented in this PR is an experimental feature currently available only under Linux x86-64.
To enable the experimental syscall sandbox the `-sandbox=<mode>` option must be passed to `bitcoind`:
```
-sandbox=<mode>
Use the experimental syscall sandbox in the specified mode
(-sandbox=log-and-abort or -sandbox=abort). Allow only expected
syscalls to be used by bitcoind. Note that this is an
experimental new feature that may cause bitcoind to exit or crash
unexpectedly: use with caution. In the "log-and-abort" mode the
invocation of an unexpected syscall results in a debug handler
being invoked which will log the incident and terminate the
program (without executing the unexpected syscall). In the
"abort" mode the invocation of an unexpected syscall results in
the entire process being killed immediately by the kernel without
executing the unexpected syscall.
```
The allowed syscalls are defined on a per thread basis.
I've used this feature since summer 2020 and I find it to be a helpful testing/debugging addition which makes it much easier to reason about the actual capabilities required of each type of thread in Bitcoin Core.
---
Quick start guide:
```
$ ./configure
$ src/bitcoind -regtest -debug=util -sandbox=log-and-abort
…
2021-06-09T12:34:56Z Experimental syscall sandbox enabled (-sandbox=log-and-abort): bitcoind will terminate if an unexpected (not allowlisted) syscall is invoked.
…
2021-06-09T12:34:56Z Syscall filter installed for thread "addcon"
2021-06-09T12:34:56Z Syscall filter installed for thread "dnsseed"
2021-06-09T12:34:56Z Syscall filter installed for thread "net"
2021-06-09T12:34:56Z Syscall filter installed for thread "msghand"
2021-06-09T12:34:56Z Syscall filter installed for thread "opencon"
2021-06-09T12:34:56Z Syscall filter installed for thread "init"
…
# A simulated execve call to show the sandbox in action:
2021-06-09T12:34:56Z ERROR: The syscall "execve" (syscall number 59) is not allowed by the syscall sandbox in thread "msghand". Please report.
…
Aborted (core dumped)
$
```
---
[About seccomp and seccomp-bpf](https://en.wikipedia.org/wiki/Seccomp):
> In computer security, seccomp (short for secure computing mode) is a facility in the Linux kernel. seccomp allows a process to make a one-way transition into a "secure" state where it cannot make any system calls except exit(), sigreturn(), and read() and write() to already-open file descriptors. Should it attempt any other system calls, the kernel will terminate the process with SIGKILL or SIGSYS. In this sense, it does not virtualize the system's resources but isolates the process from them entirely.
>
> […]
>
> seccomp-bpf is an extension to seccomp that allows filtering of system calls using a configurable policy implemented using Berkeley Packet Filter rules. It is used by OpenSSH and vsftpd as well as the Google Chrome/Chromium web browsers on Chrome OS and Linux. (In this regard seccomp-bpf achieves similar functionality, but with more flexibility and higher performance, to the older systrace—which seems to be no longer supported for Linux.)
ACKs for top commit:
laanwj:
Code review and lightly tested ACK 4747da3a5b
Tree-SHA512: e1c28e323eb4409a46157b7cc0fc29a057ba58d1ee2de268962e2ade28ebd4421b5c2536c64a3af6e9bd3f54016600fec88d016adb49864b63edea51ad838e17
fa9d72a794 Remove unused ParseDouble and ParsePrechecks (MarcoFalke)
fa3cd28535 refactor: Remove unused ParsePrechecks from ParseIntegral (MarcoFalke)
Pull request description:
All of the `ParsePrechecks` are already done by `ToIntegral`, so remove them from `ParseIntegral`.
Also:
* Remove redundant `{}`. See https://github.com/bitcoin/bitcoin/pull/20457#discussion_r720116866
* Add missing failing c-string test case
* Add missing failing test cases for non-int32_t integral types
ACKs for top commit:
laanwj:
Code review ACK fa9d72a794, good find on ParseDouble not being used at all, and testing for behavior of embedded NULL characters is always a good thing.
practicalswift:
cr ACK fa9d72a794
Tree-SHA512: 3d654dcaebbf312dd57e54241f9aa6d35b1d1d213c37e4c6b8b9a69bcbe8267a397474a8b86b57740fbdd8e3d03b4cdb6a189a9eb8e05cd38035dab195410aa7
74c0d81b46 test: use miniwallet in test_rpc() function in feature_rbf.py (Shubhankar)
Pull request description:
This PR aims to further increase MiniWallet usage in the functional test feature_rbf.py by using it in the test_rpc(...) . Sub test needs wallet to get a utxo for creating raw txn, and to get address for output, address can be hardcoded and mini wallet can be used for utxo. fund raw transaction is a wallet rpc and should be tested only when bitcoin core is compiled with wallet
ACKs for top commit:
laanwj:
Code review ACK 74c0d81b46
theStack:
tACK 74c0d81b46
Tree-SHA512: a98cc0df0fe70ee113a293cd4fd659c5bece47c17937d368193b65b150b331a2c694cdeb2792386f1a6deefb8d6750ed83ffa0ae6f9d13fa2b7625cd80bc692a
928af61cdb allow send rpc take external inputs and solving data (Andrew Chow)
e39b5a5e7a Tests for funding with external inputs (Andrew Chow)
38f5642ccc allow fundtx rpcs to work with external inputs (Andrew Chow)
d5cfb864ae Allow Coin Selection be able to take external inputs (Andrew Chow)
a00eb388e8 Allow CInputCoin to also be constructed with COutPoint and CTxOut (Andrew Chow)
Pull request description:
Currently `fundrawtransaction` and `walletcreatefundedpsbt` both do not allow external inputs as the wallet does not have the information necessary to estimate their fees.
This PR adds an additional argument to both those RPCs which allows the user to specify solving data. This way, the wallet can use that solving data to estimate the size of those inputs. The solving data can be public keys, scripts, or descriptors.
ACKs for top commit:
prayank23:
reACK 928af61cdb
meshcollider:
Re-utACK 928af61cdb
instagibbs:
crACK 928af61cdb
yanmaani:
utACK 928af61.
Tree-SHA512: bc7a6ef8961a7f4971ea5985d75e2d6dc50c2a90b44c664a1c4b0f1be5c1c97823516358fdaab35771a4701dbefc0862127b1d0d4bfd02b4f20d2befa4434700
fad5a18548 doc: Combine 23.0 release notes (MarcoFalke)
Pull request description:
`doc/release-notes-remove-rescan.md` didn't include a `(#pull_nr)`, so fix that and also combine the notes while touching them.
ACKs for top commit:
shaavan:
ACK fad5a18548
fanquake:
ACK fad5a18548
Tree-SHA512: 1528619f056197d410d0fa5415742ae303fd21b236f220451614f9ec07668a4f34a76298907378b2c4b25a405cff8cd1d205024d2f3d8f207d11900a607f765f
As the faucet will always ask for a captcha now, the current script is
no longer usable.
Change the script to print the captcha in dot-matrix to the terminal,
using unicode Braille characters.
Also:
* Remove redundant {} from return statement
* Add missing failing c-string test case and "-" and "+" strings
* Add missing failing test cases for non-int32_t integral types
b658d7d5c5 test: update assert_fee_amount() in test_framework/util.py (Jon Atack)
Pull request description:
Follow-up to 42e1b5d979 (#12486).
- update call to `round()` with our utility function `satoshi_round()` to avoid intermittent test failures
- rename `fee_per_kB` to `feerate_BTC_kvB` for precision
- store division result in `feerate_BTC_vB`
Possibly resolves#19418.
ACKs for top commit:
meshcollider:
utACK b658d7d5c5
Tree-SHA512: f124ded98c913f98782dc047a85a05d3fdf5f0585041fa81129be562138f6261ec1bd9ee2af89729028277e75b591b0a7ad50244016c2b2fa935c6e400523183
0ab4c3b272 Return false on corrupt tx rather than asserting (Samuel Dobson)
Pull request description:
Takes up #19793
Rather than asserting, we log an error and return CORRUPT so that the user is informed. This type of error isn't critical so it isn't worth `assert`ing.
ACKs for top commit:
achow101:
ACK 0ab4c3b272
laanwj:
Code review ACK 0ab4c3b272
ryanofsky:
Code review ACK 0ab4c3b272. There may be room for more improvements later like better error messages or easier recovery options, but changing from an assert to an error seems like a clear improvement, and this seems to avoid all the pitfalls of the last PR that tried this.
Tree-SHA512: 4a1a412e7c473d176c4e09123b85f390a6b0ea195e78d28ebd50b13814b7852f8225a172511a2efb6affb555b11bd4e667c19eb8c78b060c5444b62f0fae5f7a
6e1150ea3b fuzz: add guide to fuzzing with Eclipser v1.x (Alex Groce)
Pull request description:
MarcoFalke and practicalswift here's an Eclipser guide, reconstructed from their documentation and my docker history getting it up and running. It might be good if someone confirmed it actually works for them in a fresh ubuntu 20.04.
ACKs for top commit:
practicalswift:
ACK 6e1150ea3b
Tree-SHA512: ca855932fd7a2c1d1005d572ab5fabc26f42d779f9baf279783f08a43dd72ec60f57239135d30c2a82781e593626fec2c96bb19fb91e1b777cef2d83a54eba35
18c5b23a0f [test] Test that -blocksonly nodes still serve compact blocks. (Niklas Gögge)
a79ad65fc2 [test] Test that getdata(CMPCT) is still sent on regular low bandwidth connections. (Niklas Gögge)
5e231c116b [test] Test that -blocksonly nodes do not send getdata(CMPCT) on a low bandwidth connection. (Niklas Gögge)
5bf6587457 [test] Test that -blocksonly nodes do not request high bandwidth mode. (Niklas Gögge)
0dc8bf5b92 [net processing] Dont request compact blocks in blocks-only mode (Niklas Gögge)
Pull request description:
A blocks-only node does not participate in transaction relay to reduce its own bandwidth usage and therefore does not have a mempool. The use of compact blocks is not beneficial to such a node since it will always have to download full blocks.
In both high- and low-bandwidth relaying the `cmpctblock` message is sent. This represent a bandwidth overhead for blocks-only nodes because the `cmpctblock` message is several times larger in the average case than the equivalent `headers` or `inv` announcement.
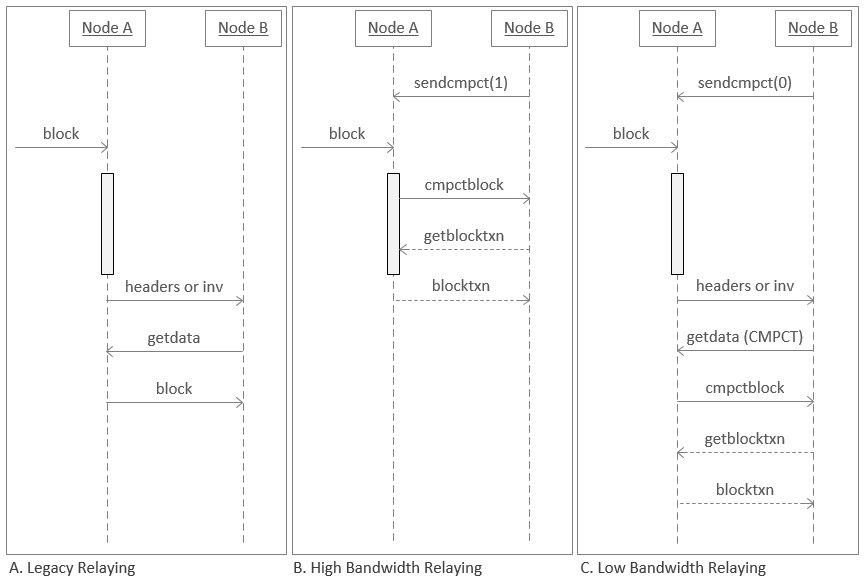
>**Example:**
>A block with 2000 txs results in a `cmpctblock` with 2000*6 bytes in short ids. This is several times larger than the equivalent 82 bytes for a `headers` message or 37 bytes for an `inv`.
## Approach
This PR makes blocks-only nodes always use the legacy relaying to download new blocks.
It does so by making blocks-only nodes never initiate a high-bandwidth block relay connection by disabling the sending of `sendcmpct(1)`. Additionally a blocks-only node will never request a compact block using `getdata(CMPCT)`.
A blocks-only node will continue to serve compact blocks to its peers in both high- and low-bandwidth mode.
ACKs for top commit:
naumenkogs:
ACK 18c5b23a0f
rajarshimaitra:
tACK 18c5b23a0f
jnewbery:
reACK 18c5b23a0f
theStack:
re-ACK 18c5b23a0f🥛
Tree-SHA512: 0c78804aa397513d41f97fe314efb815efcd852d452dd903df9d4749280cd3faaa010fa9b51d7d5168b8a77e08c8ab0a491ecdbdb3202f2e9cd5137cddc74624
8615507a4e scripted-diff: rename DBErrors::RESCAN_REQUIRED to NEED_RESCAN (Samuel Dobson)
Pull request description:
Suggested here as a trivial follow-up: https://github.com/bitcoin/bitcoin/pull/23123#discussion_r719709924
Makes RESCAN_REQUIRED consistent with NEED_REWRITE
ACKs for top commit:
achow101:
ACK 8615507a4e
jonatack:
ACK 8615507a4e
Tree-SHA512: 82d057c45e192cd6dd8a47675b52699e6cbc82272609a971e6e5d6796aad14a941a70e40d3913dbb611f79c8eadff8030c60ea6f203f2edc3720c0e78c166b97
dc3ec74d67 Add rescan removal release note (Samuel Dobson)
bccd1d942d Remove -rescan startup parameter (Samuel Dobson)
f963b0fa8c Corrupt wallet tx shouldn't trigger rescan of all wallets (Samuel Dobson)
6c006495ef Remove outdated dummy wallet -salvagewallet arg (Samuel Dobson)
Pull request description:
Remove the `-rescan` startup parameter.
Rescans can be run with the `rescanblockchain` RPC.
Rescans are still done on wallet-load if needed due to corruption, for example.
ACKs for top commit:
achow101:
ACK dc3ec74d67
laanwj:
re-ACK dc3ec74d67
Tree-SHA512: 608360d0e7d73737fd3ef408b01b33d97a75eebccd70c6d1b47a32fecb99b9105b520b111b225beb10611c09aa840a2b6d2b6e6e54be5d0362829e757289de5c
- update call to round() with satoshi_round() to avoid intermittent test failures
- rename fee_per_kB to feerate_BTC_kvB for precision
- store division result in feerate_BTC_vB
2fe69efbc6 qt, wallet: Drop no longer used WalletController::getOpenWallets() (Hennadii Stepanov)
f6991cb906 qt, wallet: Add LoadWalletsActivity class (Hennadii Stepanov)
4a024fc310 qt, wallet, refactor: Move connection to QObject::deleteLater to ctor (Hennadii Stepanov)
f9b633eeab qt, wallet: Move activity progress dialog from data member to local (Hennadii Stepanov)
Pull request description:
This PR improves the GUI responsiveness during initial wallets loading at startup (especially ones that have tons of txs), and shows a standard progress dialog for long loading:

Fixes#247.
ACKs for top commit:
ryanofsky:
Code review ACK 2fe69efbc6. Just suggested changes since last review: squashing commits and dropping unused method (thanks!)
shaavan:
reACK 2fe69efbc6
promag:
Code review ACK 2fe69efbc6.
Tree-SHA512: 2ac3cb48886e0005fc36b3fd0c2b35abd557186be16db3145d753c34d94188e4f4ff14dc07fb0fb7558944f84498204a3988f8284fd56c6d85b47bc9081e71a6
4747db8761 util: Introduce ToIntegral<T>(const std::string&) for locale independent parsing using std::from_chars(…) (C++17) (practicalswift)
Pull request description:
Make `Parse{Int,UInt}{32,64}` use locale independent `std::from_chars(…)` (C++17) instead of locale dependent `strto{l,ll,ul,ull}`.
[About `std::from_chars`](https://en.cppreference.com/w/cpp/utility/from_chars): _"Unlike other parsing functions in C++ and C libraries, `std::from_chars` is locale-independent, non-allocating, and non-throwing."_
ACKs for top commit:
laanwj:
Code review ACK 4747db8761
Tree-SHA512: 40f2cd582bc19ddcf2c498eca3379167619eff6aa047bbac2f73b8fd8ecaefe5947c66700a189f83848751f9f8c05645e83afd4a44a1679062aee5440dba880a
4446ef0a54 build: remove support for weak linking getauxval() (fanquake)
e56100c5b4 build: remove arm includes from getauxval() check (fanquake)
Pull request description:
It was [pointed out in #23030](https://github.com/bitcoin/bitcoin/pull/23030#issuecomment-922893367) that we might be able to get rid of our weak linking of [`getauxval()`](https://man7.org/linux/man-pages/man3/getauxval.3.html) (`HAVE_WEAK_GETAUXVAL`) entirely, with only Android being a potential holdout:
> I wonder if it's time to get rid of HAVE_WEAK_GETAUXVAL. I think it's confusing. Either we build against a C library that has this functionality, or not. We don't do this weak linking thing for any other symbols and recently got rid of the other glibc backwards compatibility stuff.
> Unless there is still a current platform that really needs it (Android?), I'd prefer to remove it from the build system, it has caused enough issues.
After looking at Android further, it would seem that given we are moving to using `std::filesystem`, which [requires NDK version 22 and later](https://github.com/android/ndk/wiki/Changelog-r22), and `getauxval` has been available in the since [API version 18](https://developer.android.com/ndk/guides/cpu-features#features_using_libcs_getauxval3), that shouldn't really be an issue. Support for API levels < 19 will be dropped with the NDK 24 release, and according to [one website](https://apilevels.com/), supporting API level 18+ will cover ~99% of devices. Note that in the CI we currently build with NDK version 22 and API level 28.
The other change in this PR is removing the include of headers for ARM intrinsics, from the check for strong `getauxval()` support in configure, as they shouldn't be needed. Including these headers also meant that the check would basically only succeed when building for ARM. This would be an issue if we remove weak linking, as we wouldn't detect `getauxval()` as supported on other platforms. Note that we also use `getauxval()` in our RNG when it's available.
I've checked that with these changes we detect support for strong `getauxval()` on Alpine (muslibc). On Linux, previously we'd be detecting support for weak getauxval(), now we detect strong support. Note that we already require glibc 2.17, and `getauxval()` was introduced in `2.16`.
This is an alternative / supersedes #23030.
ACKs for top commit:
laanwj:
Code review and tested ACK 4446ef0a54
Tree-SHA512: 5f2a9e9cc2d63bddab73f0dcb169d4d6beda74622af82bc0439722f1189f81d052e2fc1eaf27056a7a606320d5ddc4c11075f0d051dd93d77c5e1c15337f354a
1d44513f9b Squashed 'src/crc32c/' changes from b5ef9be675..0d624261ef (MarcoFalke)
Pull request description:
Only change is a warning fix for arm.
```
CXX crc32c/src/crc32c_libcrc32c_a-crc32c.o
In file included from crc32c/src/crc32c.cc:11:0:
crc32c/src/./crc32c_arm64_check.h: In function ‘bool crc32c::CanUseArm64Crc32()’:
crc32c/src/./crc32c_arm64_check.h:43:37: warning: the address of ‘long unsigned int getauxval(long unsigned int)’ will never be NULL [-Waddress]
unsigned long hwcap = (&getauxval != nullptr) ? getauxval(AT_HWCAP) : 0;
~~~~~~~~~~~^~~~~~~~~~
ACKs for top commit:
laanwj:
Code review ACK fac1c13ead
fanquake:
ACK fac1c13ead
Tree-SHA512: 22a52caf67dd89092eff1f075fbf5c5d16bdca9146ba042ce5d3fcc10ce1485e950964089f8536c938ebe650676e03a789d3597fe45b19920fd2c5e72f1391ad
8ff3743f5e Revert "doc: Remove outdated comments" (Hennadii Stepanov)
Pull request description:
Unfortunately, in #23094 the assumption that #14336 makes comments outdated is wrong. As pointed in https://github.com/bitcoin/bitcoin/pull/23094#discussion_r717226839, the #14336 just moved the relevant code a few lines down.
This PR reverts commit ee7891a0c4, and moves the comments into the right place.
I apologize about that.
ACKs for top commit:
MarcoFalke:
cr ACK 8ff3743f5e
laanwj:
ACK 8ff3743f5e
Tree-SHA512: 84aca627bb5b49c06fc172778f9b9407482c5a873ccbc3dc40167e6a8ad0bc60475d6a469c843b7b42712e35cf3fc2d3518923e791d5e0c59628e042acc72747
90be29c5b5 wallet: enable SQLite extended result codes (Sebastian Falbesoner)
Pull request description:
With this change, we get more fine-grained error messages if something goes wrong in the course of communicating with the SQLite database. To pick some random examples, the error codes SQLITE_IOERR_NOMEM, SQLITE_IOERR_CORRUPTFS or SQLITE_IOERR_FSYNC are way more specific than just a plain SQLITE_IOERR, and the corresponding error messages generated by sqlite3_errstr() will hence give a better hint to the user (or also to the developers, if an error report is sent) what the cause for a failure is.
See the SQLite documentation
https://www.sqlite.org/c3ref/extended_result_codes.htmlhttps://www.sqlite.org/c3ref/c_abort_rollback.html
> In its default configuration, SQLite API routines return one of 30 integer result codes. However, experience has shown that many of these result codes are too coarse-grained. They do not provide as much information about problems as programmers might like. In an effort to address this, newer versions of SQLite (version 3.3.8 2006-10-09 and later) include support for additional result codes that provide more detailed information about errors.
ACKs for top commit:
Sjors:
utACK 90be29c
achow101:
ACK 90be29c5b5
laanwj:
Code review ACK 90be29c5b5
Tree-SHA512: 2b7a60860c206f2b5f8ff9d4a7698efdee897c9ad024621b8fd165b841c20746d9780da3cf46aaf448a777e229a5b3cdf3a4792e8ef82cda9c5d46e354a9a598
451ca244db qt, refactor: Drop intermediate BitcoinApplication::shutdownResult slot (Hennadii Stepanov)
f3a17bbe5f qt: Do not exit and re-enter main event loop during shutdown (Hennadii Stepanov)
b4e0d2c431 qt, refactor: Allocate SendConfirmationDialog instances on heap (Hennadii Stepanov)
332dea2852 qt, refactor: Keep HelpMessageDialog in the main event loop (Hennadii Stepanov)
c8bae37a7a qt, refactor: Keep PSBTOperationsDialog in the main event loop (Hennadii Stepanov)
7fa91e8312 qt, refactor: Keep AskPassphraseDialog in the main event loop (Hennadii Stepanov)
6f6fde30e7 qt, refactor: Keep EditAddressDialog in the main event loop (Hennadii Stepanov)
59f7ba4fd7 qt, refactor: Keep CoinControlDialog in the main event loop (Hennadii Stepanov)
7830cd0b35 qt, refactor: Keep OptionsDialog in the main event loop (Hennadii Stepanov)
13f618818d qt: Add GUIUtil::ShowModalDialogAndDeleteOnClose (Hennadii Stepanov)
Pull request description:
On master (1ef34ee25e) during shutdown `QApplication` exits the main event loop, then re-enter again.
This PR streamlines shutdown process by removing the need to interrupt the main event loop, that is required for #59.
Also, blocking [`QDialog::exec()`](https://doc.qt.io/qt-5/qdialog.html#exec) calls are replaced with safer [`QDialog::show()`](https://doc.qt.io/qt-5/qwidget.html#show), except for `SendConfirmationDialog` as that change is not trivial (marked as TODO).
The [`QDialog::open()`](https://doc.qt.io/qt-5/qdialog.html#open) was not used because the actual modality mode (application modal or window modal) of a dialog depends on whether it has a parent.
This PR does not change behavior, and all touched dialogs are still application modal.
As a follow up, a design research could suggest to make some dialogs window modal.
NOTE for reviewers: quitting app while a dialog is open (e.g., via systray icon menu) must work fine.
ACKs for top commit:
laanwj:
Code review and lighly tested ACK 451ca244db
promag:
ACK 451ca244db, just changed signal to `quitRequested`.
Tree-SHA512: ef01ab6ed803b202e776019a4e1f592e816f7bc786e00574b25a0bf16be2374ddf9db21f0a26da08700df7ef0ab9e879550df46dcfe3b6d940f5ed02ca5f8447
2b90eae33c doc: update developer docs for subtree renaming (fanquake)
Pull request description:
Update the developer docs after the [recent subtree renaming](https://github.com/bitcoin/bitcoin/pull/22646#issuecomment-921154730).
ACKs for top commit:
hebasto:
ACK 2b90eae33c
Tree-SHA512: ed0eec8db888e60595c07f4fad0a506673e4b10345fb2dd6d1a98d785da22bddf1fe8896aa52fd67f5e1688e3c91c6b642739e08646f1b920f50f0d35037d961